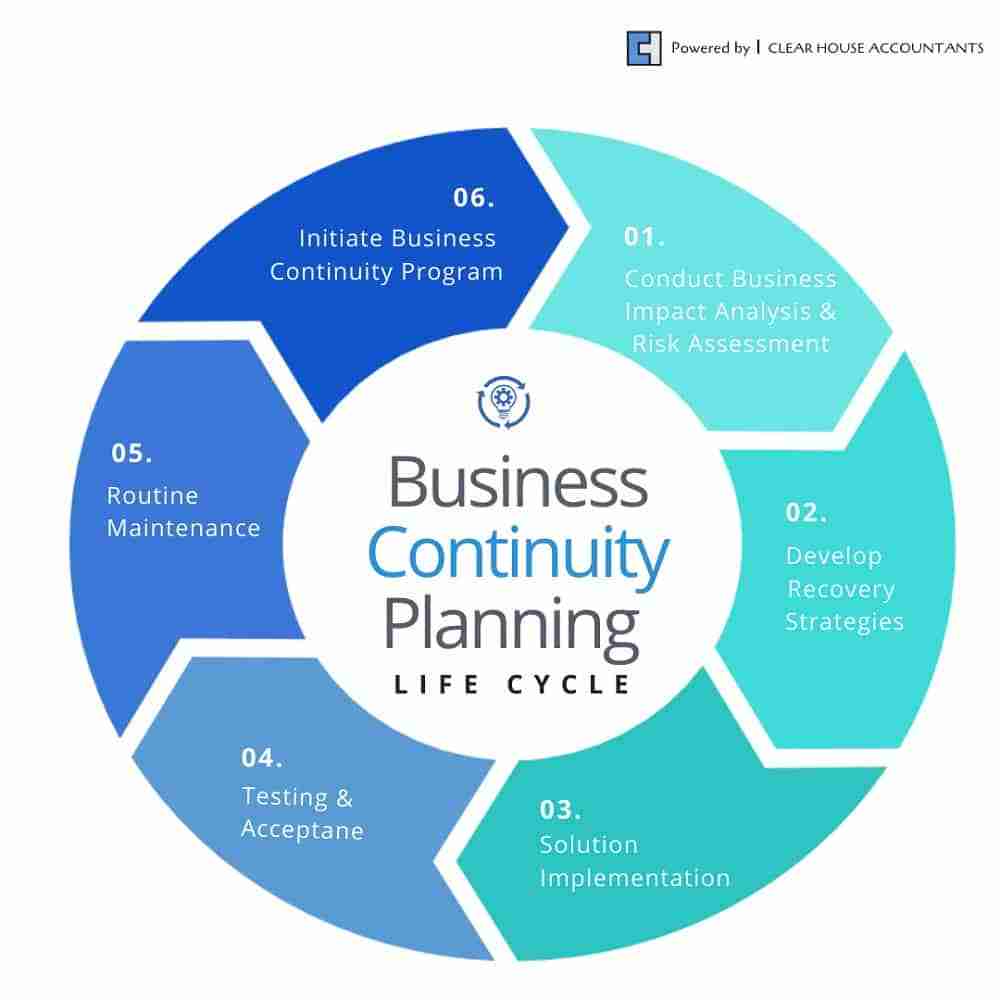
Business continuity strategy is paramount for organizational resilience. This guide explores the multifaceted nature of safeguarding operations against disruptions, from identifying vulnerabilities and implementing mitigation strategies to conducting thorough risk assessments and developing comprehensive recovery plans. We will delve into the key distinctions between business continuity, disaster recovery, and risk management, providing practical examples and actionable insights to fortify your organization’s preparedness.
Understanding and implementing a robust business continuity strategy isn’t just about surviving a crisis; it’s about thriving afterward. This involves a proactive approach to risk identification, thorough planning, rigorous testing, and consistent communication. By investing in these crucial elements, organizations can minimize downtime, protect their reputation, and ensure continued success in the face of adversity.
Defining Business Continuity Strategy
A robust business continuity strategy is crucial for organizations of all sizes to ensure operational resilience in the face of disruptions. It’s a proactive approach designed to minimize the impact of unforeseen events, allowing businesses to continue operating, albeit potentially at a reduced capacity, and recover swiftly. This strategy goes beyond simply restoring systems; it encompasses the entire organization’s ability to maintain essential functions and fulfill its mission.
A comprehensive business continuity strategy comprises several core components. These components work together to provide a layered defense against disruptions, ensuring that the organization can withstand and recover from a wide range of incidents.
Core Components of a Robust Business Continuity Strategy
The foundation of any effective business continuity strategy rests on several key elements. These elements, when properly implemented and integrated, create a resilient framework capable of withstanding significant disruptions. These elements include a thorough risk assessment identifying potential threats, a detailed business impact analysis determining the critical functions and their dependencies, the development of recovery strategies for these critical functions, a comprehensive communication plan, a robust testing and review process, and lastly, a well-defined training program for all personnel involved. The interdependency of these elements is vital for a strategy’s success.
Differences Between Business Continuity, Disaster Recovery, and Risk Management
While closely related, business continuity, disaster recovery, and risk management are distinct concepts. Risk management is the overarching process of identifying, assessing, and mitigating potential threats to an organization. Disaster recovery, on the other hand, focuses specifically on restoring IT systems and data after a disruptive event. Business continuity encompasses a broader scope, addressing the continuation of all critical business functions, including those beyond IT, during and after a disruption. It’s the holistic approach that ensures the entire organization can function, even if certain systems are offline. Think of it this way: risk management identifies the threats, disaster recovery addresses the IT aspects of a response, and business continuity ensures the entire organization remains operational.
Examples of Successful Business Continuity Strategy Implementations
Several organizations have demonstrated the effectiveness of well-executed business continuity strategies. For example, during Hurricane Sandy, many financial institutions in New York City experienced significant disruptions. However, those that had invested in robust business continuity plans, including geographically diverse data centers and robust remote work capabilities, were able to minimize the impact on their operations and quickly resume services. Similarly, companies that have successfully navigated major cyberattacks often had comprehensive plans in place, allowing them to quickly contain the breach, restore systems, and maintain customer trust. These successful implementations often involve a combination of proactive planning, regular testing and updates, and a strong commitment from leadership. The key is not just having a plan, but regularly testing and updating it to ensure its relevance and effectiveness in a dynamic environment.
Risk Assessment and Identification
A comprehensive risk assessment is the cornerstone of any robust business continuity strategy. It involves systematically identifying potential threats and vulnerabilities that could disrupt operations, analyzing their likelihood and potential impact, and developing mitigation strategies to minimize their effects. This process ensures that resources are allocated effectively to address the most critical risks, maximizing the chances of business survival during a disruptive event.
A thorough risk assessment employs both qualitative and quantitative methods to achieve a holistic understanding of potential threats. Qualitative methods focus on subjective judgments and expert opinions, while quantitative methods use numerical data and statistical analysis to provide a more precise assessment. Combining both approaches provides a more complete picture of the risk landscape.
A robust business continuity strategy considers all aspects of operational resilience. Understanding the financial impact of disruptions is crucial, and this often involves assessing the return on investment of various marketing initiatives. Accurately calculating this return is key, which is why familiarizing yourself with resources like this guide on Marketing ROI calculation is beneficial for optimizing your overall business continuity strategy and ensuring financial stability during unexpected events.
Risk Identification and Categorization
Identifying potential threats requires a systematic approach, involving brainstorming sessions with key personnel from various departments, reviewing past incidents, analyzing industry trends, and researching potential external factors such as natural disasters or cyberattacks. Once identified, these risks should be categorized based on their likelihood and potential impact. The following table provides a sample categorization, using a simple scale for both likelihood and impact. Remember that the specific scales and categories should be tailored to the specific organization and its context.
| Risk Type | Likelihood (Low, Medium, High) | Impact (Low, Medium, High) | Mitigation Strategy |
|---|---|---|---|
| Power Outage | Medium | High | Redundant power supply, generator backup |
| Cyberattack | Medium | High | Robust cybersecurity measures, regular security audits, incident response plan |
| Natural Disaster (Flood) | Low | High | Offsite data backup, disaster recovery site |
| Key Personnel Loss | Medium | Medium | Cross-training, succession planning |
Qualitative and Quantitative Risk Assessment Techniques
Qualitative risk assessment relies on expert judgment and experience to evaluate the likelihood and impact of risks. Techniques include brainstorming sessions, SWOT analysis, and Delphi method (gathering expert opinions anonymously). Quantitative risk assessment uses numerical data and statistical analysis to assign probabilities and potential losses to identified risks. Techniques include fault tree analysis (FTA), event tree analysis (ETA), and Monte Carlo simulation. For instance, a company might use historical data on the frequency of power outages in its location to quantify the likelihood of this risk.
Risk Registers and Their Importance
A risk register is a central repository that documents all identified risks, their likelihood, impact, mitigation strategies, and assigned owners. It serves as a living document, continuously updated as new risks emerge or existing ones change. A well-maintained risk register is crucial for effective risk management and business continuity planning. It facilitates communication and collaboration among stakeholders, tracks progress on mitigation efforts, and provides a readily accessible source of information for decision-making during a crisis. A typical risk register might include columns for Risk ID, Risk Description, Likelihood, Impact, Risk Score (calculated from likelihood and impact), Mitigation Strategy, Owner, Status, and Target Completion Date. The consistent update and review of this register is key to the effectiveness of the business continuity plan.
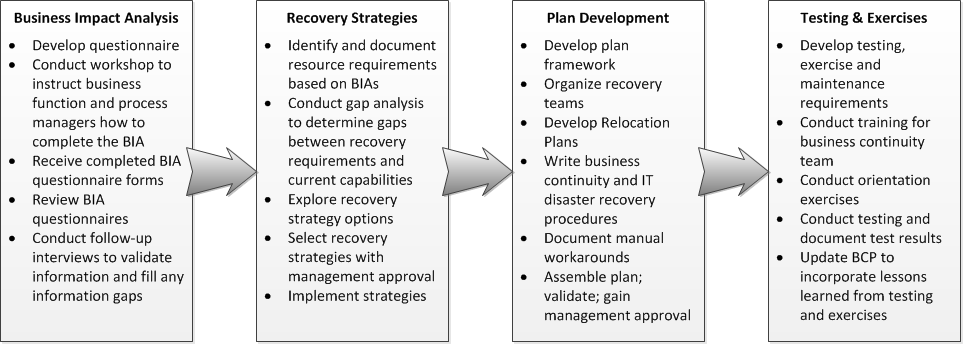
Business Impact Analysis (BIA)
A Business Impact Analysis (BIA) is a crucial component of any robust business continuity strategy. It systematically identifies critical business functions and assesses the potential impact of disruptions on those functions. The results of a BIA inform the development of recovery strategies, ensuring that resources are allocated effectively to protect the most vital aspects of the business. This process helps organizations prioritize their recovery efforts and set realistic recovery time and point objectives.
A BIA involves a structured process of identifying critical business functions, analyzing their dependencies, and determining the potential consequences of disruptions. This analysis helps determine the acceptable downtime for each function and the maximum acceptable data loss. The output informs the creation of recovery strategies and resource allocation decisions.
Defining Critical Business Functions
The first step in performing a BIA is to clearly define the organization’s critical business functions. These are the functions absolutely necessary for the organization to continue operating at an acceptable level during and after a disruption. This identification often involves collaboration with various departments and stakeholders to gain a comprehensive understanding of the organization’s operations. For example, in a retail business, critical functions might include sales processing, inventory management, and customer service. A manufacturing company might prioritize production, supply chain management, and quality control. Each function needs careful evaluation.
Determining Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs)
Once critical business functions are identified, the next step is to determine their Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs). The RTO represents the maximum acceptable downtime for a given function before significant negative impacts occur. The RPO defines the maximum acceptable data loss in the event of a disruption. For example, a financial institution might have a very low RTO and RPO for its transaction processing system, while a marketing department might have a higher tolerance for downtime.
To illustrate, consider a hospital. The RTO for emergency room services would likely be measured in minutes, reflecting the critical nature of these services. The RPO for patient medical records would also be very low, perhaps measured in hours, to minimize the risk of data loss. Conversely, a less critical function like staff training might have a much higher RTO and RPO. Determining these objectives requires careful consideration of the potential consequences of downtime and data loss for each function.
Sample BIA Report
A BIA report should clearly present the findings of the analysis in a concise and easily understandable format. The following is a sample structure:
Executive Summary
Brief overview of the BIA process, key findings, and recommendations.
Methodology
Description of the methods used to conduct the BIA, including data sources and stakeholder involvement.
Critical Business Functions
- Sales Processing
- Inventory Management
- Customer Service
- Order Fulfillment
- Financial Reporting
Impact Analysis
A table detailing the potential impact of disruptions on each critical business function, including estimated financial losses, reputational damage, and legal liabilities. This section would also include the calculated RTOs and RPOs for each function. For example, a disruption to Sales Processing could lead to a loss of $X per hour, while a disruption to Customer Service could lead to a decrease in customer satisfaction and potential loss of future business.
Recommendations
Specific recommendations for mitigating the risks identified in the BIA, including the development of recovery strategies, resource allocation, and training programs. For example, implementing redundant systems, establishing offsite data backups, and developing detailed recovery procedures.
Visual Representation of BIA Results
The results of a BIA can be effectively presented to stakeholders using various visual aids. A heatmap, for instance, could visually represent the criticality of different business functions based on their RTOs and RPOs. Functions with low RTOs and RPOs would be represented by darker colors, highlighting their importance. A bar chart could show the estimated financial impact of downtime for each function. These visuals help stakeholders quickly grasp the key findings and prioritize recovery efforts. A clear and concise presentation of the findings is crucial for securing buy-in from stakeholders and ensuring that the necessary resources are allocated to support the business continuity plan.
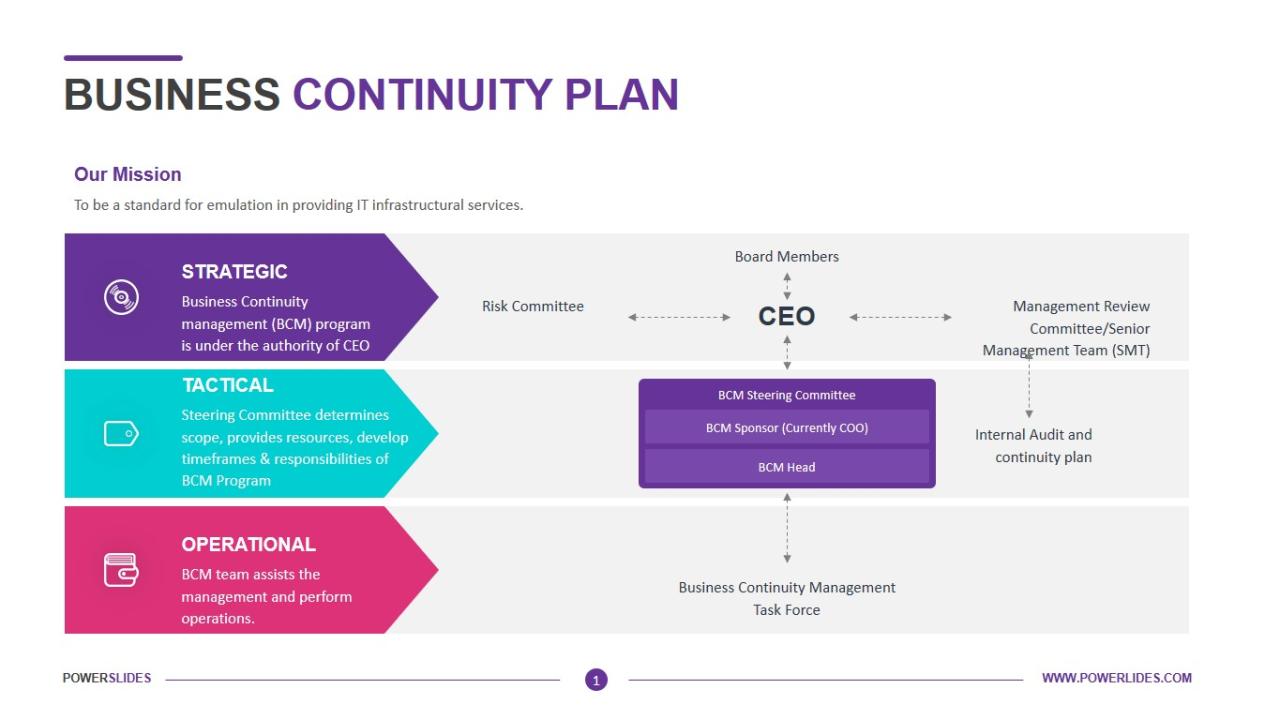
Developing a Business Continuity Plan
A robust Business Continuity Plan (BCP) translates the findings from the Risk Assessment and Business Impact Analysis into actionable steps. It Artikels procedures to ensure business operations can continue, or quickly resume, following a disruptive event. This plan should be detailed, regularly tested, and readily accessible to all relevant personnel.
The BCP serves as a comprehensive guide, providing clear instructions and responsibilities to minimize downtime and maintain operational resilience. It’s a living document, requiring regular review and updates to reflect changing business needs and emerging threats.
Communication Procedures
Effective communication is paramount during a crisis. The BCP should detail communication channels, escalation procedures, and contact lists for key personnel, including internal teams and external stakeholders (e.g., clients, suppliers). This includes specifying methods for disseminating information (e.g., email, SMS, phone calls, public address systems) and establishing a central communication hub for managing information flow. Regular communication drills should be conducted to ensure familiarity and efficiency.
Resource Allocation Strategies
The plan should Artikel procedures for allocating resources, including financial resources, personnel, technology, and physical assets, during a disruption. This involves pre-identifying alternative resources and establishing clear priorities for resource allocation based on the impact of the disruption and the criticality of business functions. For instance, a company might prioritize restoring its customer service systems before resuming less critical operations.
Crisis Management Protocols
A well-defined crisis management protocol is crucial. The BCP should detail procedures for handling various types of disruptions, including natural disasters, cyberattacks, and pandemics. This includes defining roles and responsibilities for crisis management team members, outlining decision-making processes, and establishing procedures for incident reporting, investigation, and resolution. Regular crisis management simulations should be conducted to test the plan’s effectiveness.
Decision-Making Flowchart During Business Disruption, Business continuity strategy
Imagine a flowchart with a central starting point representing the detection of a disruptive event. Branches would then lead to different decision points based on the nature of the disruption (e.g., power outage, cyberattack, natural disaster). Each decision point would have options leading to specific actions, such as activating the emergency response team, implementing backup systems, or contacting relevant authorities. The flowchart would ultimately guide the organization towards restoring essential business functions and minimizing the impact of the disruption. The flowchart should clearly show the escalation path for decisions requiring approvals at higher management levels.
Recovery Strategies
Several recovery strategies can be implemented to mitigate the impact of disruptions.
- Failover: This involves automatically switching to a backup system or location in the event of a primary system failure. For example, a company might have a secondary data center in a different geographic location to take over if the primary data center is affected by a natural disaster.
- Backup: Regular backups of data and systems are crucial for quick recovery. This includes creating copies of critical data and storing them in a secure and accessible location, either on-site or off-site. Regular testing of backups is vital to ensure their integrity and functionality.
- Redundancy: Redundancy involves creating duplicate systems or components to ensure continued operation even if one component fails. This could include having multiple servers, network connections, or power sources. For example, a company might use redundant internet connections from two different providers to ensure continuous connectivity.
The choice of recovery strategy depends on factors such as the nature of the potential disruption, the criticality of the affected business function, and the cost of implementing the strategy. A cost-benefit analysis should be conducted to determine the most appropriate strategy for each scenario.
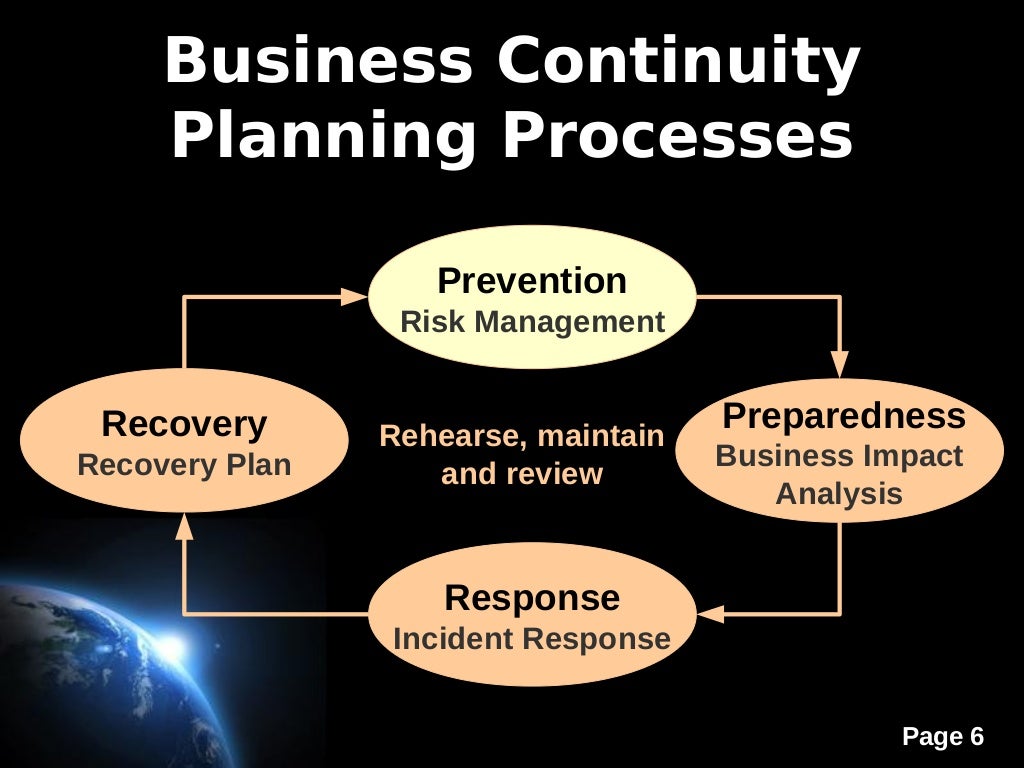
Testing and Maintenance
A robust business continuity plan is only as good as its implementation and ongoing maintenance. Regular testing and review are crucial to ensure the plan remains relevant, effective, and capable of mitigating potential disruptions. Without these processes, the plan risks becoming outdated and ineffective, failing to provide the necessary support during a real crisis.
Testing the business continuity plan involves a multifaceted approach, utilizing various methodologies to assess its effectiveness across different scenarios and organizational levels. This iterative process of testing, reviewing, and updating ensures the plan’s continued relevance and adaptability to evolving threats and organizational changes. It also provides valuable training opportunities for personnel, reinforcing their understanding of their roles and responsibilities during a disruptive event.
Testing Methodologies
A comprehensive testing strategy should incorporate a range of methodologies to thoroughly evaluate the plan’s effectiveness. Different methods offer unique insights into various aspects of the plan, identifying strengths and weaknesses that may not be apparent through a single approach. Combining these methods provides a holistic assessment, ensuring that the plan can withstand a variety of potential disruptions.
- Tabletop Exercises: These exercises involve a facilitated discussion among key personnel, walking through various hypothetical scenarios and evaluating the plan’s response. They are relatively low-cost and allow for quick identification of gaps in the plan. For example, a tabletop exercise might simulate a cyberattack, focusing on the response procedures Artikeld in the plan and identifying any ambiguities or missing steps.
- Functional Exercises: These involve testing specific functions or systems Artikeld in the business continuity plan. This could include testing the backup and recovery of critical data or the functionality of a secondary data center. A functional exercise could focus on restoring access to critical applications within a specified recovery time objective (RTO).
- Full-Scale Simulations: These are more intensive exercises that involve a significant portion of the organization and mimic a real-world disruptive event. They are resource-intensive but provide the most realistic test of the plan’s effectiveness. A full-scale simulation could involve evacuating a building and setting up operations at a secondary location, testing the entire plan from start to finish.
Plan Reviews and Updates
Regular reviews and updates are essential to maintain the plan’s relevance and effectiveness. Changes in the business environment, technology, regulatory requirements, and organizational structure necessitate periodic revisions. These updates should be incorporated into a formal review cycle, with a designated team responsible for overseeing the process. For example, annual reviews should be conducted to assess the plan’s alignment with current business priorities and to incorporate any lessons learned from past incidents or exercises.
Key Performance Indicators (KPIs)
Monitoring the effectiveness of the business continuity plan requires the establishment of relevant KPIs. These metrics provide quantifiable data to assess the plan’s performance and identify areas for improvement. Tracking these KPIs provides insights into the plan’s efficiency and helps to demonstrate its value to stakeholders.
- Recovery Time Objective (RTO): The maximum acceptable downtime for a critical business function after a disruptive event. A lower RTO indicates better plan effectiveness.
- Recovery Point Objective (RPO): The maximum acceptable data loss in the event of a disruption. A lower RPO indicates better data protection strategies.
- Mean Time To Recovery (MTTR): The average time it takes to restore a business function after a disruption. A lower MTTR demonstrates faster recovery capabilities.
- Plan Compliance Rate: The percentage of employees who have completed the necessary training and understand their roles and responsibilities under the plan.
- Exercise Participation Rate: The percentage of key personnel who participated in the testing and training exercises.
Communication and Training
Effective communication and thorough training are paramount to a successful business continuity strategy. Without a well-defined communication plan and trained personnel, even the most meticulously crafted plan can falter during a crisis. These elements ensure that everyone understands their roles, responsibilities, and how to react effectively, minimizing disruption and maximizing the chances of a swift recovery.
A robust communication and training program bridges the gap between a theoretical plan and its practical implementation, transforming it from a document into a living, operational strategy. It fosters a culture of preparedness and ensures the organization can respond cohesively and efficiently to unforeseen events.
Internal and External Communication Plan
A comprehensive communication plan Artikels how information will be disseminated both internally (to employees, management, and other stakeholders within the organization) and externally (to clients, suppliers, investors, and regulatory bodies) during a crisis. This plan should detail communication channels, frequency of updates, designated spokespersons, and escalation procedures. For example, a company might utilize email, SMS alerts, internal messaging platforms, and a dedicated website for internal communications, while relying on press releases, social media, and direct contact with key external stakeholders for external updates. The plan must also specify the type of information to be shared and who is responsible for creating and disseminating it. This ensures consistent messaging and prevents the spread of misinformation.
Employee Training Program
A well-structured training program educates employees on their specific roles and responsibilities within the business continuity plan. This program should include interactive exercises, simulations, and role-playing scenarios to ensure that employees understand their actions during a crisis and can effectively perform their assigned tasks. For instance, a training session might involve a simulated power outage, requiring employees to follow established procedures for data backup, system recovery, and communication with clients. The training should also cover the use of emergency communication systems, security protocols, and any specific procedures relevant to their roles. Regular refresher training should be implemented to maintain proficiency and adapt to changes in the business environment.
Ensuring Consistent Communication
Maintaining consistent communication across all organizational levels during a disruption requires establishing clear communication channels and protocols. A centralized communication hub, perhaps a dedicated crisis management team, is essential to coordinate information flow. This team would be responsible for verifying information, creating consistent messaging, and distributing updates through the pre-defined channels. The use of standardized templates and communication protocols can further ensure consistency and prevent ambiguity. Regular communication drills and simulations allow the organization to test its communication systems and identify potential weaknesses before a real crisis occurs. This proactive approach ensures that the communication plan is not only well-defined but also effectively executed when needed.
Technology and Infrastructure
A robust technological infrastructure is the bedrock of any effective business continuity strategy. The ability to maintain operations during and after a disruptive event hinges heavily on the resilience and adaptability of your IT systems. This section will explore the crucial role of technology in ensuring business continuity, highlighting key solutions and their importance.
Technology plays a multifaceted role in supporting business continuity, acting as both a potential point of failure and a critical tool for mitigation and recovery. The right technological investments can significantly reduce downtime, minimize data loss, and accelerate the return to normal operations following a disruption. Conversely, a poorly planned or inadequately secured IT infrastructure can exacerbate the impact of an incident, potentially leading to irreversible damage.
Cloud Computing
Cloud computing offers significant advantages for business continuity. By migrating critical applications and data to the cloud, businesses can achieve greater scalability, flexibility, and redundancy. Cloud providers typically offer multiple geographically dispersed data centers, ensuring business continuity even in the event of a regional outage. For example, a company using Amazon Web Services (AWS) can leverage AWS’s global infrastructure to seamlessly switch operations to a different region if their primary data center is affected by a natural disaster. This geographic redundancy ensures minimal disruption to operations. Furthermore, cloud-based solutions often include built-in disaster recovery features, such as automated failover and replication, which further enhance resilience.
Virtualization
Virtualization allows for the creation of multiple virtual machines (VMs) on a single physical server. This technology enhances resource utilization and provides a layer of abstraction that simplifies disaster recovery. In the event of a server failure, virtual machines can be quickly restored to a different physical server or to the cloud, minimizing downtime. For instance, a company running its customer relationship management (CRM) system on a virtual machine can easily migrate the VM to a backup server in case of a hardware failure, ensuring continuous access to critical customer data.
Data Backup and Recovery Solutions
Regular data backups are essential for business continuity. A comprehensive backup strategy should encompass multiple backup methods, including local backups, offsite backups, and cloud backups. Data recovery solutions should be tested regularly to ensure their effectiveness. The 3-2-1 backup rule—three copies of data, on two different media, with one copy offsite—is a widely accepted best practice. Failing to adhere to a robust data backup and recovery strategy can result in significant data loss and potentially irreversible damage to the business. For example, a retail company losing its sales data due to a ransomware attack could face significant financial losses if they lack a reliable backup and recovery mechanism.
Robust IT Infrastructure and Disaster Recovery Solutions
A robust IT infrastructure is the foundation of a successful business continuity strategy. This includes reliable hardware, redundant network connections, and secure data centers. Disaster recovery solutions, such as hot sites, warm sites, and cold sites, provide alternative locations for business operations in the event of a disaster. A hot site is a fully equipped facility that can immediately resume operations, while a cold site requires more time to set up. The choice of disaster recovery solution depends on the organization’s recovery time objective (RTO) and recovery point objective (RPO). For example, a financial institution with stringent RTO and RPO requirements might opt for a hot site, while a smaller business with less critical operations might choose a warm or cold site. Regular testing of disaster recovery plans is crucial to ensure their effectiveness.
Technology Solutions Enhancing Business Resilience
Several technology solutions can significantly enhance business resilience. These include high-availability clustering, which ensures continuous operation even if one server fails; load balancing, which distributes traffic across multiple servers to prevent overload; and geographic redundancy, which replicates data and applications across multiple locations. Implementing these technologies can significantly reduce the impact of disruptions and ensure business continuity. For example, a web-hosting company utilizing high-availability clustering and load balancing can maintain its website’s availability even during periods of high traffic or server failures. Geographic redundancy protects against regional outages or natural disasters.
Legal and Regulatory Compliance
A robust business continuity strategy must inherently consider and adhere to all relevant legal and regulatory frameworks. Failure to do so can result in significant financial penalties, reputational damage, and even legal action. Integrating legal and regulatory compliance into the business continuity plan ensures the organization operates within the bounds of the law while maintaining operational resilience.
Legal and regulatory requirements impacting business continuity vary significantly depending on industry, location, and the nature of the business. For example, financial institutions face stricter regulations regarding data protection and operational resilience than, say, a small retail business. Understanding these specific requirements is paramount to building an effective and compliant plan.
Relevant Legal and Regulatory Requirements
Identifying applicable laws and regulations is the first step. This involves a thorough review of all relevant legislation, including data protection acts (like GDPR or CCPA), industry-specific regulations (e.g., HIPAA for healthcare), and environmental regulations (depending on the business operations). It also includes examining any local, regional, or national laws that govern business operations and disaster recovery. This review should be conducted by legal counsel and relevant internal stakeholders to ensure a comprehensive understanding.
Ensuring Compliance with Requirements
Compliance is achieved through a multi-faceted approach. This includes embedding legal and regulatory requirements directly into the business continuity plan, creating specific procedures to address compliance obligations during disruptions, and conducting regular audits to verify adherence. Training employees on relevant laws and regulations is crucial. The business continuity plan should detail specific roles and responsibilities for ensuring compliance, especially during crisis situations. For instance, a designated compliance officer could be responsible for overseeing the legal aspects of the recovery process.
Consequences of Non-Compliance
Non-compliance can lead to severe repercussions. These can range from substantial fines and penalties imposed by regulatory bodies to legal action from affected parties. Reputational damage can also be significant, impacting customer trust and investor confidence. In extreme cases, non-compliance can lead to business closure or even criminal charges. The cost of non-compliance far outweighs the investment in establishing and maintaining a legally compliant business continuity plan. Consider the example of a financial institution failing to comply with data protection regulations; the resulting fines and reputational damage could be catastrophic.
Supply Chain Continuity
A resilient supply chain is paramount to overall business continuity. Disruptions in the supply chain can have cascading effects, impacting production, sales, and ultimately, the bottom line. Integrating supply chain resilience into the broader business continuity strategy ensures that the organization can withstand and recover from disruptions affecting its suppliers, logistics, and distribution networks.
Supply chain risk management involves proactively identifying potential vulnerabilities and developing mitigation strategies to minimize their impact. This includes understanding dependencies on key suppliers, assessing potential disruptions like natural disasters, geopolitical instability, or pandemics, and establishing alternative sourcing options or contingency plans. A robust approach allows for a swift and efficient response to disruptions, minimizing downtime and maintaining operational continuity.
Identifying and Mitigating Supply Chain Risks
Identifying and mitigating supply chain risks requires a multi-faceted approach. This includes conducting thorough supplier risk assessments, mapping the supply chain to understand dependencies, and establishing key risk indicators (KRIs) to monitor potential disruptions. Regular reviews and updates of this assessment are crucial, as supply chain dynamics are constantly evolving. Mitigation strategies should be tailored to specific risks and include measures such as diversifying suppliers, holding safety stock, developing alternative sourcing options, and establishing strong communication channels with key suppliers. Scenario planning, simulating various disruptions, can help refine mitigation strategies and test their effectiveness. For instance, a company reliant on a single supplier in a geographically vulnerable area might mitigate this risk by securing a secondary supplier in a different region.
Key Suppliers, Potential Disruptions, and Mitigation Strategies
| Key Supplier | Potential Disruptions | Mitigation Strategies | Contingency Plan |
|---|---|---|---|
| XYZ Manufacturing (Raw Materials) | Natural disaster impacting production facility; Supplier bankruptcy; Political instability in region | Diversify sourcing to include ABC Manufacturing; Negotiate long-term contracts with guaranteed minimum supply; Establish safety stock levels. | Utilize existing inventory; Secure emergency supplies from secondary supplier; Explore alternative raw materials. |
| DEF Logistics (Transportation) | Port congestion; Transportation strikes; Fuel price volatility; Severe weather events | Utilize multiple transportation modes (e.g., rail, trucking); Negotiate flexible contracts with transportation providers; Implement fuel hedging strategies; Develop alternative transportation routes. | Negotiate expedited shipping; Explore alternative transportation providers; Utilize existing inventory to buffer delays. |
| GHI Distribution (Warehousing) | Warehouse fire; Power outages; Cybersecurity breaches; Labor disputes | Implement robust fire safety measures; Invest in backup power generators; Implement robust cybersecurity protocols; Maintain strong relationships with warehouse staff. | Utilize backup warehouse facilities; Secure temporary storage solutions; Implement data backup and recovery systems. |
Closing Notes: Business Continuity Strategy
Developing a successful business continuity strategy requires a holistic approach, encompassing risk assessment, impact analysis, plan development, testing, and ongoing maintenance. By proactively identifying and mitigating potential threats, organizations can significantly reduce the impact of disruptions and ensure the continuity of their critical operations. Remember, a well-executed business continuity strategy is not a static document; it’s a dynamic process that requires regular review, updates, and employee training to remain effective and relevant in an ever-changing environment.
A robust business continuity strategy anticipates various disruptions, ensuring operational resilience. Planning for unforeseen events requires a structured approach, much like crafting a compelling narrative; understanding the intricacies of storytelling, as detailed in this helpful guide on Cara menulis skrip film , can surprisingly inform the process. A well-defined continuity plan, therefore, mirrors a well-structured script, outlining potential scenarios and responses to maintain business operations.