Secure payment gateways are the unsung heroes of e-commerce, silently ensuring that online transactions are safe and secure. This guide delves into the intricate world of secure payment processing, exploring everything from the core functionality and various types of gateways to the crucial security measures and regulatory compliance needed for seamless and trustworthy online payments. We’ll examine different technologies, compare popular options, and look towards the future of secure online transactions.
Understanding secure payment gateways is vital for businesses operating online. This involves not only choosing the right gateway for your needs but also implementing robust security practices and adhering to relevant regulations. This comprehensive overview aims to equip you with the knowledge necessary to navigate the complexities of secure online payments and protect both your business and your customers.
Defining Secure Payment Gateways
Secure payment gateways are the critical link between a merchant’s website or application and the payment processors, enabling secure online transactions. They act as a secure intermediary, protecting sensitive customer data during the payment process and ensuring a smooth and reliable checkout experience. This functionality is vital for building trust and fostering customer loyalty in the increasingly digital marketplace.
At their core, secure payment gateways process payment information, encrypting sensitive data like credit card numbers and personal details to prevent unauthorized access. They validate transactions, manage fraud prevention, and facilitate the transfer of funds between the customer and the merchant. This intricate process ensures the security and integrity of financial transactions.
Types of Secure Payment Gateways
Payment gateways can be broadly categorized into hosted and self-hosted solutions. Hosted gateways are managed by the payment processor, offering a simplified setup and maintenance process. The merchant doesn’t need to manage the server infrastructure or handle the complexities of PCI DSS compliance. Self-hosted gateways, on the other hand, require the merchant to manage their own server and infrastructure, offering greater control but demanding more technical expertise and responsibility for security. The choice between these depends on the merchant’s technical capabilities and risk tolerance.
Payment Gateway Technologies
Several key technologies underpin the security of payment gateways. PCI DSS compliance is a crucial aspect, requiring merchants to adhere to stringent security standards to protect cardholder data. Tokenization is another vital technology, replacing sensitive card details with non-sensitive tokens, reducing the risk of data breaches. Other technologies, such as encryption and advanced fraud detection systems, further enhance the security of the payment process. The strength of these security measures directly impacts the level of trust and security offered to both the merchant and the customer.
Comparison of Popular Secure Payment Gateways
The following table compares four popular secure payment gateways, highlighting their features, pricing models, and security certifications. The specific features and pricing may vary depending on the chosen plan and transaction volume.
| Gateway | Features | Pricing Model | Security Certifications |
|---|---|---|---|
| Stripe | Wide range of payment methods, robust API, fraud prevention tools, recurring billing | Transaction-based fees, varying by region and payment method | PCI DSS Level 1 |
| PayPal | Global reach, buyer protection, seller protection, easy integration | Transaction-based fees, varying by region and payment method | PCI DSS Level 1 |
| Square | Point-of-sale (POS) integration, mobile payment processing, inventory management | Transaction-based fees, varying by region and payment method | PCI DSS Level 1 |
| Authorize.Net | Comprehensive payment processing solutions, recurring billing, fraud detection | Monthly fees, transaction-based fees, varying by features and transaction volume | PCI DSS Level 1 |
Security Measures in Payment Gateways
Secure payment gateways employ a multi-layered approach to protect sensitive financial data during online transactions. These measures are crucial for maintaining user trust and preventing fraud. The effectiveness of a payment gateway hinges on its ability to consistently and reliably safeguard both the merchant and the customer.
Encryption in Securing Payment Transactions
Encryption is the cornerstone of secure payment processing. It involves converting readable data (plaintext) into an unreadable format (ciphertext) using a cryptographic algorithm and a key. Only the recipient possessing the correct decryption key can access the original data. Common encryption protocols used in payment gateways include Transport Layer Security (TLS) and Secure Sockets Layer (SSL), which encrypt data transmitted between the user’s browser and the payment gateway server. This ensures that sensitive information like credit card numbers and personal details remain confidential during transmission, preventing eavesdropping and interception by malicious actors. The strength of the encryption depends on the key length and the algorithm used; stronger encryption, such as AES-256, provides significantly higher security.
Two-Factor Authentication in Payment Gateway Security
Two-factor authentication (2FA) adds an extra layer of security beyond the traditional username and password. It requires users to provide two distinct forms of verification to prove their identity. This might involve a password and a one-time code sent to their mobile phone via SMS or a dedicated authentication app, or a password and a biometric scan (fingerprint or facial recognition). 2FA significantly reduces the risk of unauthorized access, even if a hacker obtains the user’s password. By requiring a second factor, 2FA makes it substantially harder for attackers to gain access to accounts and initiate fraudulent transactions. For example, even if someone steals your password, they would still need access to your phone or biometric data to complete the login.
Common Vulnerabilities and Mitigation Strategies in Payment Gateways
Payment gateways, despite robust security measures, are not immune to vulnerabilities. SQL injection attacks, where malicious code is injected into database queries to manipulate data, are a common threat. Cross-site scripting (XSS) attacks allow attackers to inject malicious scripts into websites, potentially stealing user data. Another significant vulnerability is insufficient input validation, where the gateway fails to properly check and sanitize user inputs, leading to potential data breaches or system crashes. Mitigation strategies include robust input validation, regular security audits and penetration testing, employing web application firewalls (WAFs) to filter malicious traffic, and keeping software and systems up-to-date with security patches. Furthermore, implementing a strong security information and event management (SIEM) system allows for real-time monitoring and detection of suspicious activities.
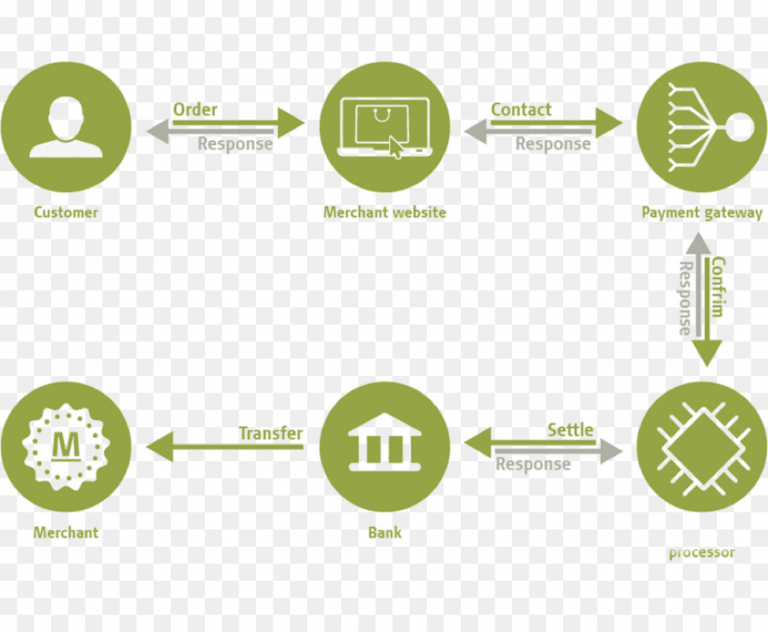
Secure Payment Transaction Flowchart, Secure payment gateway
The following describes a secure payment transaction flowchart. Imagine a visual representation, a series of boxes connected by arrows.
Box 1: Customer Initiates Transaction: The customer adds items to their online shopping cart and proceeds to checkout.
Arrow: Points to Box 2.
Box 2: Payment Gateway Integration: The merchant’s website redirects the customer to the secure payment gateway.
Arrow: Points to Box 3.
Box 3: Customer Enters Payment Details: The customer securely enters their payment information (credit card details, etc.) on the gateway’s secure page. Encryption is active during this step.
Arrow: Points to Box 4.
Box 4: Payment Gateway Processes Transaction: The gateway validates the payment information, communicates with the payment processor (e.g., Visa, Mastercard), and verifies the transaction. 2FA may be implemented here.
Arrow: Points to Box 5.
Box 5: Transaction Authorization: The payment processor authorizes the transaction.
Arrow: Points to Box 6.
Box 6: Confirmation and Redirection: The gateway confirms the successful transaction to the merchant and redirects the customer back to the merchant’s website.
Arrow: Points to Box 7.
Box 7: Order Completion: The merchant completes the order and updates the order status.
Integration and Implementation

Integrating a secure payment gateway into your e-commerce platform is crucial for smooth transactions and maintaining customer trust. This process involves several steps, from setting up a merchant account to configuring the gateway within your chosen platform. Careful planning and execution are key to a seamless integration.
Best Practices for Integrating a Secure Payment Gateway
Successfully integrating a payment gateway requires a strategic approach. Prioritize choosing a gateway compatible with your existing e-commerce platform and possessing robust security features. Thoroughly test the integration in a staging environment before deploying it to your live website to prevent disruptions and ensure a flawless user experience. Regularly monitor transaction data and security logs to identify and address potential vulnerabilities promptly. Furthermore, keep your payment gateway software updated to benefit from the latest security patches and performance enhancements. Finally, ensure compliance with all relevant Payment Card Industry Data Security Standard (PCI DSS) regulations.
Setting Up a Merchant Account
A merchant account is a business bank account that allows you to accept credit and debit card payments. The process typically involves applying with a payment processor or acquiring bank, providing necessary business documentation (such as articles of incorporation, tax ID, and bank statements), and undergoing a background check. Once approved, you’ll receive merchant account credentials, including a merchant ID and API keys, necessary for connecting your e-commerce platform to the payment gateway. The application process can take several days or weeks depending on the provider and the complexity of your business structure. Be prepared to provide information about your business’s history, anticipated transaction volume, and risk profile.
Configuring a Secure Payment Gateway for Various Platforms
The configuration process varies depending on the e-commerce platform.
WordPress
Many WordPress plugins facilitate payment gateway integration. Popular options include WooCommerce with its extensive payment gateway extensions, or dedicated plugins for specific gateways like Stripe or PayPal. The process generally involves installing and activating the plugin, configuring the plugin settings with your merchant account credentials, and testing the integration to ensure functionality. Detailed instructions are usually provided within the plugin’s documentation.
Shopify
Shopify offers a streamlined integration process through its app store. Numerous payment gateway apps are available, including Shopify Payments (Shopify’s own gateway), Stripe, and PayPal. Installation usually involves adding the app from the Shopify app store, connecting it to your merchant account, and configuring settings specific to the chosen gateway. Shopify’s user-friendly interface simplifies the process, requiring minimal technical expertise.
Essential Considerations When Choosing and Implementing a Payment Gateway
Selecting and implementing a payment gateway requires careful consideration of several factors. These include the gateway’s fees, supported payment methods, security features, ease of integration, customer support, and compliance with relevant regulations. Consider the transaction volume your business anticipates and choose a gateway capable of handling that volume without performance issues. Also, assess the gateway’s reputation for reliability and security, checking for reviews and testimonials from other businesses. Finally, ensure the gateway supports the payment methods preferred by your target audience.
Compliance and Regulations: Secure Payment Gateway
Secure payment gateways operate within a complex regulatory landscape designed to protect sensitive financial data and consumer privacy. Adherence to these regulations is not merely a best practice; it’s a legal and ethical imperative that safeguards both the business and its customers. Non-compliance can lead to significant financial penalties, reputational damage, and loss of customer trust.
Understanding and implementing the necessary security measures to meet these requirements is crucial for maintaining a secure and reliable payment processing system.
PCI DSS Compliance
The Payment Card Industry Data Security Standard (PCI DSS) is a comprehensive set of security standards designed to ensure that ALL companies that accept, process, store or transmit credit card information maintain a secure environment. Failure to comply can result in hefty fines, potential legal action, and the loss of the ability to process card payments. PCI DSS compliance involves a multi-faceted approach, including regular security assessments, vulnerability scanning, and the implementation of robust security controls. The specific requirements depend on the level of involvement with cardholder data.
GDPR Compliance
The General Data Protection Regulation (GDPR) is a European Union regulation that governs the processing of personal data, including payment information. It focuses on data privacy and the rights of individuals regarding their data. For payment gateways processing data from EU citizens, compliance with GDPR is mandatory. This includes obtaining explicit consent for data processing, ensuring data security, and providing individuals with the ability to access, rectify, and erase their data. Non-compliance can result in significant fines.
Ensuring Compliance with Payment Gateway Regulations
Choosing a reputable payment gateway provider is a foundational step. Reputable providers are proactive in maintaining compliance with PCI DSS and GDPR, regularly undergoing audits and implementing the necessary security controls. This significantly reduces the burden on the merchant. Beyond provider selection, internal procedures are crucial. This includes regular security assessments, employee training on security best practices, and the implementation of strong access controls to limit who can access sensitive data. Maintaining accurate records of all security measures and audits is also essential for demonstrating compliance.
Key Compliance Requirements and Their Practical Implementation
The following list highlights key compliance requirements and provides examples of their practical implementation:
- Strong Passwords and Access Control: Implement strong password policies and multi-factor authentication to restrict access to sensitive data. Implementation: Require complex passwords with regular changes, use MFA (e.g., Google Authenticator), and limit access based on the principle of least privilege.
- Regular Security Assessments and Vulnerability Scanning: Conduct regular vulnerability scans and penetration testing to identify and address security weaknesses. Implementation: Utilize automated scanning tools and engage qualified security professionals for penetration testing at least annually.
- Data Encryption: Encrypt sensitive data both in transit and at rest. Implementation: Use HTTPS for secure communication and encrypt databases using strong encryption algorithms (e.g., AES-256).
- Secure Coding Practices: Develop and maintain secure coding practices to prevent vulnerabilities in custom applications. Implementation: Employ secure coding guidelines (OWASP), conduct code reviews, and use static and dynamic analysis tools.
- Incident Response Plan: Develop and regularly test an incident response plan to effectively handle security breaches. Implementation: Define roles and responsibilities, establish communication protocols, and conduct regular drills to ensure preparedness.
Future Trends in Secure Payment Gateways
The landscape of secure payment gateways is constantly evolving, driven by technological advancements and shifting consumer preferences. The future promises even more sophisticated security measures, seamless user experiences, and innovative payment methods. This section explores key trends shaping the future of this critical component of online commerce.
Biometric Authentication and Blockchain Technology
Biometric authentication, utilizing unique physiological or behavioral characteristics like fingerprints, facial recognition, or voice patterns, is rapidly gaining traction. This technology offers a significantly enhanced layer of security compared to traditional password-based systems, reducing the risk of unauthorized access and fraudulent transactions. Blockchain technology, with its decentralized and immutable ledger, presents another promising avenue for enhancing security and transparency in payment processing. By recording transactions on a distributed network, blockchain can make it virtually impossible to alter or delete payment records, improving accountability and reducing the likelihood of fraud. For example, some payment platforms are already exploring the use of blockchain to streamline cross-border payments and reduce transaction fees.
The Impact of Mobile Payments
Mobile payments, facilitated by smartphones and other mobile devices, are transforming how consumers make purchases. The increasing adoption of near-field communication (NFC) technology and mobile wallets like Apple Pay and Google Pay is driving the demand for secure payment gateways that can seamlessly integrate with these mobile platforms. This trend necessitates payment gateways that are optimized for mobile devices, offering user-friendly interfaces and robust security protocols to protect sensitive data transmitted over mobile networks. The rise of mobile payments also necessitates the development of advanced fraud detection systems capable of identifying and preventing fraudulent transactions originating from mobile devices.
Challenges and Opportunities
The future of secure payment gateways is not without its challenges. The increasing sophistication of cyberattacks necessitates the continuous development and implementation of advanced security measures. Maintaining compliance with evolving regulations and data privacy laws across different jurisdictions presents another significant hurdle. However, these challenges also present significant opportunities. The demand for secure and convenient payment solutions is constantly growing, creating a fertile ground for innovation and expansion in the payment gateway market. Companies that can effectively address the security and regulatory challenges will be well-positioned to capitalize on these opportunities.
A Hypothetical Future Secure Payment System
Imagine a future payment system leveraging a combination of technologies to provide unparalleled security and convenience. This system would utilize multi-factor authentication, combining biometric verification (fingerprint scan) with a one-time password generated by a secure authentication app. Transactions would be processed through a blockchain-based payment network, ensuring transparency and immutability. The system would also incorporate advanced machine learning algorithms to detect and prevent fraudulent transactions in real-time, analyzing vast amounts of data to identify suspicious patterns and anomalies. Furthermore, this system would be designed with strong encryption protocols and regularly updated security patches to stay ahead of evolving threats. User data would be protected under rigorous privacy policies, adhering to the highest global standards, and stored using advanced encryption methods. This hypothetical system represents a vision of a secure and efficient future for payment processing, balancing convenience and security in an increasingly digital world.